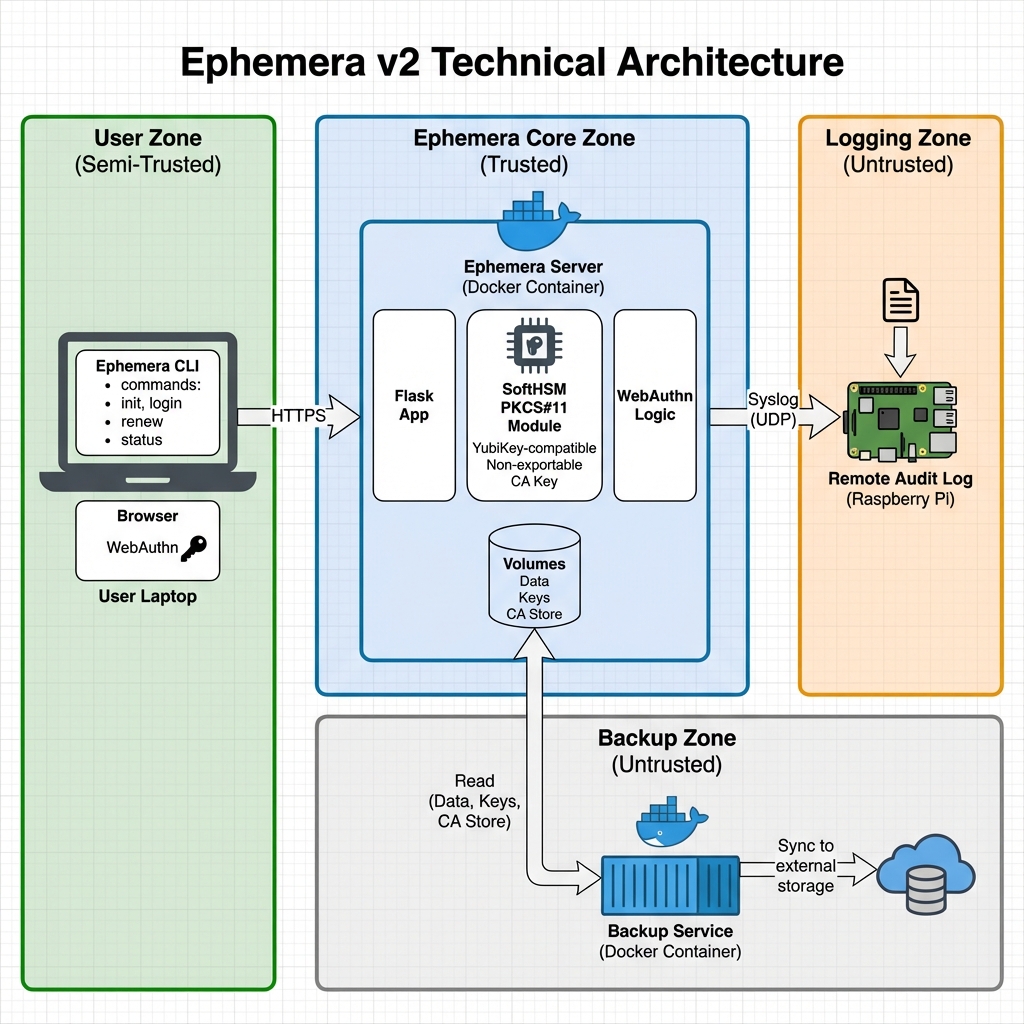
Architecture
Zero-Trust model where no long-lived SSH keys exist on user devices.
Disclosure
This diagram reflects the current implementation. Some operational hardening details
are intentionally omitted from public documentation.
Components
| Component | Role |
|---|---|
| Flask Server | Handles authentication, MFA verification, and certificate signing requests. |
| OpenSSH CA | Signs user public keys with a generated CA key. Certificates expire in minutes. |
| WebAuthn | Provides phishing-resistant MFA using hardware keys or biometrics. |
| Audit Ledger | Hash-chained log of all issuance events. Tamper-evident by design. |
Security Properties
- CA Key — Encrypted at rest, never leaves the container. Stored with 0400 permissions.
- Audit — Tamper-evident ledger with optional remote syslog mirroring.
- Ephemeral — Certificates expire in minutes by default (configurable via policy).
Trust Zones
The CA private key is the root of trust. It is generated at startup if missing and stored
in a Docker volume (/app/ca_store). The volume is never exposed to unprivileged
containers.
Certificate issuance requires successful WebAuthn or TOTP verification. The audit ledger records every issuance with a cryptographic chain to detect tampering.
Diagram